
Emotet is currently among the most prevalent and destructive types of malware in existence.
Recent modifications make it even more dangerous, but there are steps users can take to help protect themselves (please see below), including making sure you back up your computer and regularly update antivirus programs to insure they cover the latest threats.
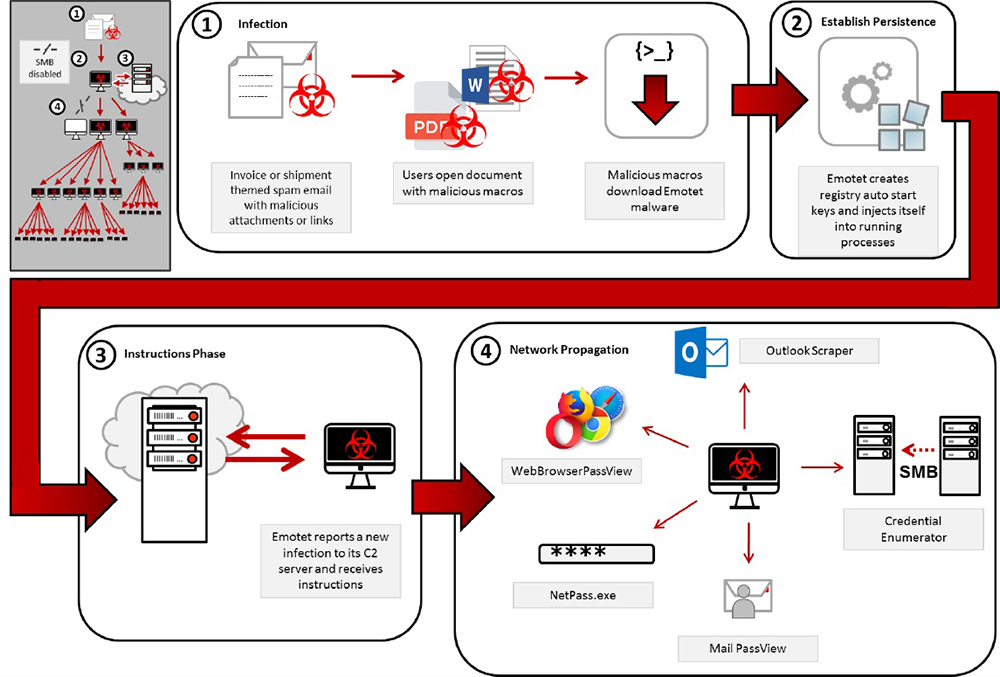
Emotet is a banking Trojan that can steal data, such as logins and passwords stored in web browsers. It's also often used to deliver malware to computers and networks. Infected systems contact the hacker's command and control server to receive updates and new malware.
Emotet is commonly spread by email, through attachments that contain malware and embedded URLs. The emails may appear to come from people or institutions that you trust, although in many cases these accounts themselves have been compromised. This method helps hackers trick people into clicking on attachments or links that infect their machine.
Some of the most recent campaigns imitate receipts, shipping notifications, or "past-due" invoices from different organizations.
If Emotet infects a computer connected to a network, it will try to infect other machines on the network by exploiting unpatched vulnerabilities. This is another reason to make sure your computer's operating system and anti-virus protections are regularly updated with the latest patches.
Emotet currently uses five known spreader modules, according to the Multi-State Information Sharing & Analysis Center:
NetPass.exe: a legitimate utility developed by NirSoft that recovers all network passwords stored on a system for the current logged-on user. This tool can also recover passwords stored in the credentials file of external drives.
Outlook scraper: a tool that scrapes names and email addresses from the victim's Outlook accounts and uses that information to send out additional phishing emails from the compromised accounts.
WebBrowserPassView: a password recovery tool that captures passwords stored by Internet Explorer, Mozilla Firefox, Google Chrome, Safari, and Opera and passes them to the credential enumerator module.
Mail PassView: a password recovery tool that reveals passwords and account details for various email clients such as Microsoft Outlook, Windows Mail, Mozilla Thunderbird, Hotmail, Yahoo! Mail, and Gmail and passes them to the credential enumerator module.
Credential enumerator: a self-extracting RAR file containing two components, a bypass and a service component. The bypass component is used for enumeration of network resources and either finds writable share drives using Server Message Block (SMB) or tries to brute force user accounts, including the administrator account. Once an available system is found, Emotet then writes the service component on the system, which writes Emotet onto the disk. Access to SMB can result in entire domains (servers and clients) becoming infected.
You can take the following steps to help prevent an Emotet infection:
- Use a regularly updated antivirus program and take advantage of automatic updates of signatures and software.
- Make sure your computer and network router have the most recent patches and updates.
- Regularly back up your computer to an external drive and disconnect the storage device from the internet after each backup. That will help ensure you have a clean copy of your files if your computer becomes infected.
- Do not visit un-trusted websites or follow links provided by unknown or un-trusted sources.
- Don't click on links or attachments in emails unless you were expecting to receive the email. If you're uncertain, contact the person or institution purportedly sending the email. Do not use phone numbers included in the email. Find the correct number on your own.
SOURCE: MS-ISAC
